Practice the attack with guidance
Get a modern cybersecurity education worth your time.
You didn’t struggle to pick up web dev or programming once you
found the resource that clicked for you.
Learn cybersecurity with just as much ease and efficiency.

Want to skip the CTF grind? Be ready for bug bounties by the end of a single course.
Hours of scrubbing through long-winded videos (recorded in one take) can’t beat learning by exploiting vulns in our engaging practical labs.
Attack Wordpress plugins, a Git service, and more real software to prepare you to crush bug bounties. When automated tools can’t cut it (nobody wants brute-forcing on their servers), learn to intelligently discover vulns.
We demystify vulnerabilities both old and new (so new that other platforms barely scratch the surface). You get clear, full explanations, down to the guts of the source code. So you’ll know how to find and exploit those bugs before everyone else.
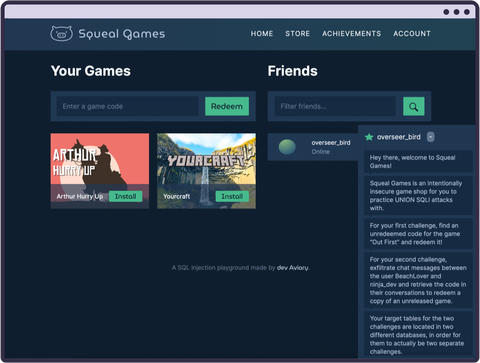
Weaponize SQL injections to leak game codes at our Squeal Games lab in the Comprehensive SQL Injection course.

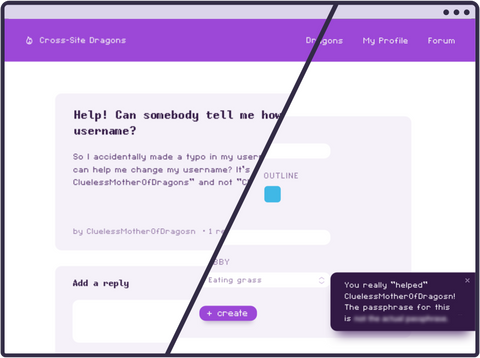
Dual-wield XSS exploits & social engineering at our Cross-Site Dragons lab in the Comprehensive XSS course.
Not all cybersec experts can teach. We can.
Don’t let your time and passion be eroded by experts without teaching expertise. See how we’ve designed our courses with evidence-based learning techniques (spaced repetition!) and years of experience.
How we teach each vulnerability
Learn the inner workings of the vulnerability
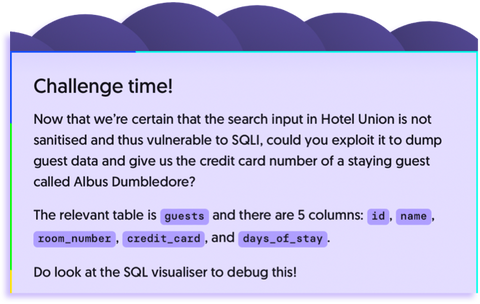
Practice the attack on real vulnerable software
Tackle full scenarios on your own, combining everything you’ve learned

Review a summary of the material, and onto the next vulnerability in the course!
Never stay stuck for long with 1-on-1 support and guidance.
Come to our daily office hours and never be alone in your studies. We are dedicated to supporting you through your journey and will personally answer every email.
How it works.
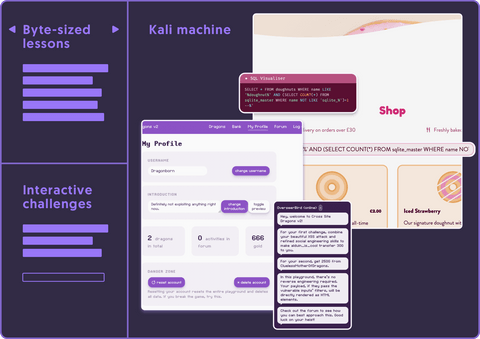
 Byte-sized lessons
Byte-sized lessons
We guide you through labs and case studies with clear explanations and helpful tips. All the gory details and source code included!
 Kali machine
Kali machine
Interact with your own virtual machine loaded with all the pentesting tools you’ll need for the courses you own, right in the browser. Unlimited hours.
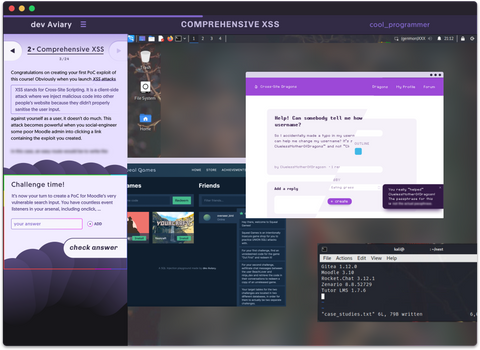
 Interactive exercises
Interactive exercises
Prove your mastery by answering questions that check your understanding of the material. Action reinforces learning.
 Practical labs
Practical labs
Solve a series of challenging, fun practical labs—each designed to help you master the exploits you’ve learned.
 Real-world case studies
Real-world case studies
Experience actual vulnerabilities out in the wild and test your skills against them. We’ve resurrected relevant case studies for you to exploit.
Preview your courses.
purchase once or subscribe to get them all
WiFi & Bluetooth Security
Reverse Engineering
Get notified when new courses are ready!
TIP : use email alias services when possible to maximise your privacy.
Simple pricing.
FAQs.
Kali machineWhat are the specs for my Kali Linux virtual machine?
Internet is disabled, CPU is limited to 1.5 units and RAM is limited to 2G. But other than that, you have access to your machine 24/7.
Will my data (my files, scripts etc) be persisted in my Kali machine?
Store all your scripts & data in ~/nest as this folder (and nothing else!) will be persisted across restarts & updates.
All your servers are too far from me and my machine is laggy. Can you set one up near me?
Of course! Let us know where you’d like your lab to be hosted and we’d happily create a new server near it.
We’re also already working on making servers in the US available.
How long do I get access to the machine?
Subscribers get access for as long as you’re subscribed. If you’ve purchased a course, then you always have access to it.
Can I request additional tools on my machine?
Of course you can! Please contact us with your requests (see our help centre when logged in).
Are there any minimum requirements to run this?
Since there’s an entire machine in our app, make sure your screen is big enough (1920x1680)!
Can I change the location of my machine & labs any time?
Send us your request via the help center when logged in. This will be automated soon!
What’s the refund policy?
We give refunds if requested within 1 month (i.e. for the current month of subscription, or courses purchased less than a month ago).
Are there prerequisites to your courses?
As long as you have a general tech background (programmer, IT, computer science student etc), we don’t assume any prior cybersecurity knowledge!
Why do you require a general tech background for your courses?
Being able to break / exploit something comes from knowing it as well as you know your palm. We leave the prerequisite tech background to other people’s capable hands, so that we can focus on teaching you how to break the tech.



